Imagine this: You're sitting in your cozy living room, sipping coffee, while controlling your smart thermostat or checking your security camera feeds from your phone. Sounds cool, right? But what if I told you there's a secure way to access those IoT devices remotely using SSH web access? Let's dive into the world of SSH web access for IoT devices examples and see how it can revolutionize the way you interact with your smart gadgets.
SSH web access might sound like a techy buzzword, but it's actually a game-changer for anyone working with IoT devices. Whether you're a tech enthusiast, a small business owner, or just someone who loves smart home automation, understanding SSH web access can help you manage your IoT devices securely from anywhere in the world. No more worrying about hackers or unauthorized access—SSH has got your back.
In this guide, we’ll break down everything you need to know about SSH web access for IoT devices. From basic concepts to real-world examples, we’ll make sure you’re well-equipped to secure your smart devices without breaking a sweat. So grab your favorite drink, and let’s get started!
Read also:Damian Hardung The Rising Star Whorsquos Turning Heads
Table of Contents
- What is SSH?
- Why SSH Web Access for IoT Devices?
- IoT Devices Examples That Support SSH
- How Does SSH Work for IoT Devices?
- Benefits of Using SSH for IoT Devices
- Security Considerations for SSH Web Access
- Tools and Software for SSH Web Access
- Setting Up SSH for IoT Devices
- Real-World Examples of SSH Web Access
- Conclusion and Next Steps
What is SSH?
Let’s start with the basics, shall we? SSH stands for Secure Shell, and it’s basically a protocol that lets you securely connect to remote devices over a network. Think of it as a secret tunnel that encrypts all the data flowing between you and the device you’re accessing. It’s like having a private conversation in a crowded room—nobody else can listen in.
SSH was originally designed for server management, but guess what? It’s now being used for IoT devices too. Why? Because IoT devices are often connected to the internet, and without proper security, they’re like open doors for hackers. SSH adds an extra layer of protection, making sure your devices stay safe and sound.
A Brief History of SSH
SSH was first introduced in the mid-90s by a Finnish computer scientist named Tatu Ylönen. Back then, internet security wasn’t as advanced as it is today, so Tatu created SSH to provide a secure way to log into remote systems. Fast forward to today, and SSH is still one of the most trusted protocols for secure communication. Cool, huh?
Why SSH Web Access for IoT Devices?
Now, you might be wondering, “Why bother with SSH web access when there are so many other ways to control IoT devices?” Great question! Let me break it down for you:
First off, SSH web access offers a level of security that most other methods just can’t match. It uses encryption to protect your data, which means even if someone intercepts your connection, they won’t be able to make sense of it. Plus, SSH supports authentication, so only authorized users can access your devices.
Secondly, SSH is super flexible. You can use it to manage a wide range of IoT devices, from smart cameras and thermostats to industrial sensors and robotics. And the best part? It works on pretty much any platform, whether you’re using Windows, macOS, or Linux.
Read also:Chris Brown Mom And Dad The Untold Story Behind The Music Icons Family
Comparison with Other Methods
Let’s compare SSH with some other popular methods for accessing IoT devices:
- HTTP/HTTPS: While HTTPS is encrypted, it’s not designed specifically for secure remote access. Plus, setting up HTTPS can be a bit of a hassle.
- FTP/SFTP: FTP is great for file transfer, but it’s not secure unless you use SFTP, which is basically FTP over SSH.
- Telnet: Avoid this one at all costs! Telnet sends data in plain text, which means anyone can snoop on your connection.
See the difference? SSH is the clear winner when it comes to secure and reliable IoT device access.
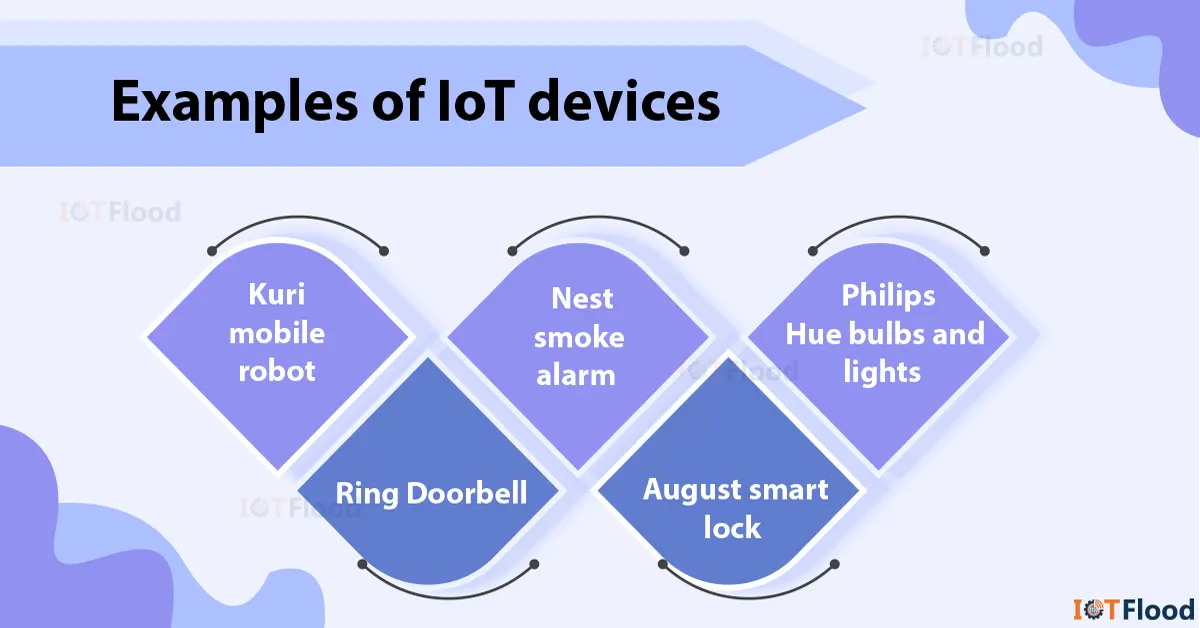
IoT Devices Examples That Support SSH
So, what kind of IoT devices can you use SSH with? The list is pretty long, but here are some common examples:
- Smart Home Devices: Think smart thermostats, lighting systems, and security cameras.
- Industrial IoT Devices: Sensors, actuators, and control systems used in manufacturing and automation.
- Healthcare IoT Devices: Wearable health monitors, remote patient monitoring systems, and medical equipment.
- Smart Agriculture Devices: Soil sensors, weather stations, and irrigation systems.
And that’s just the tip of the iceberg. Pretty much any IoT device with a processor and network connectivity can support SSH. The key is finding the right software or firmware that enables SSH functionality.
Popular IoT Platforms with SSH Support
Here are a few IoT platforms that offer built-in SSH support:
- Raspberry Pi: A favorite among hobbyists and developers, Raspberry Pi comes with SSH enabled by default.
- Arduino Yún: Combines the power of Arduino with Linux, making it perfect for SSH-based projects.
- ESP32: A versatile microcontroller with WiFi and Bluetooth capabilities, ESP32 can be configured to support SSH.
How Does SSH Work for IoT Devices?
Alright, let’s get a bit technical. When you use SSH to access an IoT device, here’s what happens:
- Connection Initiation: You start by initiating a connection to the device’s IP address or hostname using an SSH client.
- Authentication: The device will ask for your credentials, which could be a password or a public key.
- Encryption: Once authenticated, SSH establishes an encrypted tunnel between your device and the IoT device.
- Command Execution: You can now send commands to the IoT device and receive responses securely.
It’s like magic, but with science. And the best part? All this happens in the background, so you don’t have to worry about the nitty-gritty details.
SSH Protocols and Versions
SSH has evolved over the years, and there are currently two main versions:
- SSH-1: The original version, now considered outdated and insecure.
- SSH-2: The current standard, offering better security and more features.
Always use SSH-2 when working with IoT devices. Trust me, your future self will thank you.
Benefits of Using SSH for IoT Devices
Now that you know how SSH works, let’s talk about why it’s such a great choice for IoT device access:
- Enhanced Security: SSH encrypts all data, making it nearly impossible for hackers to intercept your connection.
- Remote Access: With SSH, you can manage your IoT devices from anywhere in the world, as long as you have an internet connection.
- Automation: SSH can be used to automate tasks, such as firmware updates or data collection, saving you time and effort.
- Flexibility: SSH works with a wide range of devices and platforms, making it a versatile choice for IoT projects.
And let’s not forget the peace of mind that comes with knowing your devices are secure. Who doesn’t love that?
Real-World Benefits
Here’s a quick story to illustrate the power of SSH: A small business owner in Florida uses SSH to remotely monitor and manage the HVAC systems in his chain of restaurants. Not only does this save him time and money, but it also ensures that his customers are always comfortable. Now that’s what I call smart business!
Security Considerations for SSH Web Access
While SSH is a secure protocol, it’s not foolproof. Here are a few things to keep in mind:
- Strong Passwords: Use complex passwords or public key authentication to prevent brute-force attacks.
- Firewall Rules: Limit SSH access to specific IP addresses or networks to reduce the risk of unauthorized access.
- Regular Updates: Keep your SSH software and firmware up to date to protect against vulnerabilities.
Security is a team effort, so always stay vigilant and follow best practices.
Common SSH Attacks and How to Prevent Them
Here are some common SSH attacks and how you can defend against them:
- Brute-Force Attacks: Use fail2ban or similar tools to block repeated login attempts.
- Man-in-the-Middle Attacks: Always verify the device’s fingerprint before connecting.
- Configuration Errors: Double-check your SSH settings to ensure they’re secure.
By taking these precautions, you can significantly reduce the risk of security breaches.
Tools and Software for SSH Web Access
There are plenty of tools and software available to help you set up SSH web access for your IoT devices. Here are a few popular ones:
- PuTTY: A free and easy-to-use SSH client for Windows users.
- OpenSSH: A widely used open-source SSH implementation available on most Linux and macOS systems.
- Termius: A cross-platform SSH client with a user-friendly interface.
No matter which tool you choose, make sure it’s reliable and secure. After all, your IoT devices are only as secure as the tools you use to manage them.
Choosing the Right Tool
When selecting an SSH tool, consider factors like ease of use, compatibility, and security features. For example, if you’re managing multiple IoT devices, a tool with session management capabilities might be a better fit. Do your research and choose wisely!
Setting Up SSH for IoT Devices
Ready to get your hands dirty? Here’s a step-by-step guide to setting up SSH for your IoT devices:
- Enable SSH on Your Device: Check the device’s documentation to see how to enable SSH. Most devices have this option in their settings menu.
- Install an SSH Client: Download and install an SSH client on your computer or mobile device.
- Connect to the Device: Use the SSH client to connect to your device’s IP address or hostname.
- Authenticate: Enter your credentials when prompted.
- Start Managing: Once connected, you can start sending commands and managing your device.
It’s that simple! With SSH, you’ll be managing your IoT devices like a pro in no time.
Troubleshooting Tips
Having trouble setting up SSH? Here are a few tips to help you out:
- Check Network Connectivity: Make sure your device is connected to the internet and reachable from your computer.
- Verify SSH Settings: Double-check that SSH is enabled and properly configured on your device.
- Update Firmware: Sometimes, outdated firmware can cause issues. Update